How To Conduct A Vulnerability Assessment
As well as regardless of firm size, there are intrinsic benefits to obtaining a fresh point of view on your systems, avoiding the knowledge that any type of in-house team will certainly currently have with the systems they're examining. A brand-new set of eyes will generally detect something brand-new that your internal team might not otherwise reveal.
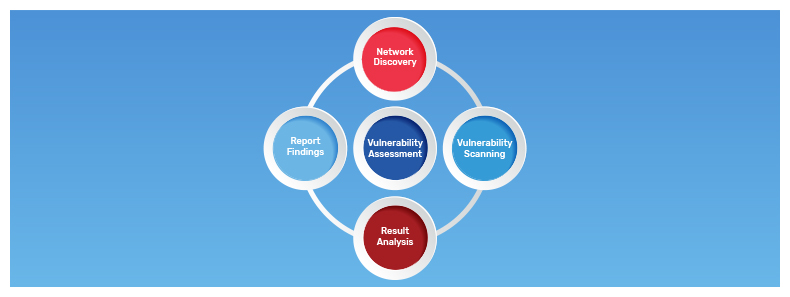
You need to begin by establishing which systems and networks will certainly be evaluated (including mobile and cloud), identifying where any sensitive data lives, and which data and also systems are most critical. Make certain that everyone included has the very same assumptions of what the assessment will certainly give, as well as ensure that lines of communication will stay open throughout the process.
Especially with a very first analysis, the variety of susceptabilities found can be frustrating which is where step 3 is available in. An even more detailed evaluation then complies with, supplying a clear feeling of the reasons for the susceptabilities, their potential impact, and the suggested techniques of removal. Each susceptability is after that rated or ranked based upon the information in jeopardy, the severity of the problem, and the damage that could be triggered by a breach of the affected system.
The Art Of Network Vulnerability Assessment
Ultimately, the vulnerability analysis causes an initiative to spot crucial imperfections, whether simply through a product update or through something a lot more entailed, from the installation of new safety tools to an improvement of protection treatments. The ranking in action 3 will help prioritize this process, making sure that the most urgent imperfections are taken care of initially.
Vulnerability analyses need to be performed on a routinely scheduled basis, quarterly at the very least (ideally month-to-month or once a week), as any type of solitary evaluation is just a picture of that minute in time. Having those pictures or reports to refer to over a duration of time will additionally offer you a strong sense of just how your safety and security posture has established, for better or for worse.
If you're carrying out at least a first vulnerability analysis in-house, which can be a logical very first step even if you're preparing to resort to a third-party vendor in the future, you have a wide variety of software application to select from. incredible Dallas IT company If you're looking to a third-party vendor, an ever-growing series of suppliers and also services are now supplying vulnerability assessments.
Network Vulnerability Assessment And Penetration Testing
Beginning by obtaining a sense of the depth of their experience (especially with business of your size and also in your market) as well as guarantee that their service and also reporting completely match your requirements including any kind of governing conformity you call for. Lots of vulnerability scanning and also protection screening vendors additionally offer solutions, as well as MSSPs are also a good place to look.
Vulnerability analyses are a needed component of your cyber security due to the fact that they reveal you where your operating system's weak points are. If you don't know where those weaknesses are or exactly how many of them your network has, then you could fall prey to vicious cyber assaults. After all, you can not quit hacking from making use of a vulnerability you don't learn about.
Vulnerability Assessment
All companies need a way to find susceptabilities on their networks. This is specifically real for bigger services and also those with delicate databanking, federal government, finance, regulation, wellness care, and also education and learning are all markets in which safeguarding network information and also framework is paramount. But smaller companies have to additionally ensure their details is protected, without pouring all their IT time and also resources into the task.
So, what are the most effective susceptability scanners on the marketplace today? In this short article, I evaluate the leading vulnerability scanners, both paid and also cost-free. Network Setup Manager sticks out as my choice for finest total device, as it provides not only important tracking insights however also a means to take care of setup problems swiftly throughout mass devices.
Nonetheless you pick to spend your resources, a fundamental understanding of network susceptability management is crucial. This post also lays out the fundamentals of vulnerability monitoring every IT pro requires to know so you obtain the most benefits out of your scanning tool. Do you know if your IT framework is protected? Also if end users can currently access their data and also your network connection appears fine, you can not think the safety of your network.
Vulnerability Assessment
The goal is to decrease these susceptabilities as high as possible, which is a recurring job, considering your network is constantly made use of and also changed while safety and security threats continuously evolve. Vulnerability management has lots of parts. You could believe mounting antivirus software program, for example, suffices, when as a matter of fact, it often tends to leave you playing troubleshooting.
Vulnerability scanning tools can make a distinction. Basically, susceptability scanning software program can assist IT safety and security admins with the following tasks. Admins need to be able to recognize security openings in their network, across workstations, web servers, firewall programs, as well as much more. It takes automated software program to catch as most of these susceptabilities as feasible.
Not all vulnerabilities are equally immediate. Scanning devices can classify and categorize susceptabilities to assist admins prioritize the most worrisome problems. When you have actually determined concern dangers, resolving them can be a complicated task. The best device can aid you automate the procedure of provisioning tools. Even after vulnerabilities have been attended to, it's still important for admins to show compliance with relevant policies.